.well-known/security.txt
How to Allow /.well-known/security.txt in .htaccessПодробнее

Security.txt demoПодробнее

What is Security.txt? Does Security.txt Affects SEO?Подробнее
Bug bounty bits: Security.txt for finding a targetПодробнее

Create security.txt in the root of your application to help ethical hackersПодробнее

NDSS 2022 MADWeb - Characterizing the Adoption of Security.txt Files and their Applications to Vu,,,Подробнее

what is the security.txt fileПодробнее
Security.txt - My Awesome Invention for Security ResearchersПодробнее

How to Access Well Known Security txt fileПодробнее
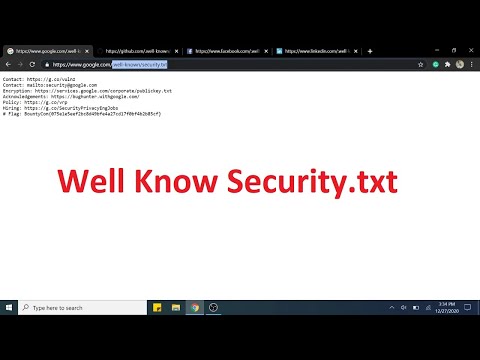
Security.txt: Pros, Cons & Ethical HackingПодробнее

CLOUDFLARE INTRODUCES SECURITY.TXT SETUP WIZARD: A NEW SECURITY STANDARD #CLOUDFLARE #serverПодробнее

Known vulnerabilities vs misconfigurationsПодробнее

How was rockyou.txt created? rockyou.txt explained #cybersecurity #securitybreach #leak #rockyouПодробнее
Cybersecurity Performance Goals for Critical Infrastructure: A Primer and A Progress ReportПодробнее

A Developer Guide to Reporting VulnerabilitiesПодробнее

SECURITY.TXT | Cyber Security com Renato Buiú | EP. 54Подробнее

Robots.txt Explained In Under a Minute - Cybersecurity Basics #birds #cute #webdevelopmentПодробнее
How to Install security.txt Extension in Plesk | Step-by-Step TutorialПодробнее
What Is A TXT Record? - SecurityFirstCorp.comПодробнее

Wat is security.txt?Подробнее
